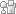From:
dbaportal.eu
(Thanks to alesk for his great job)
Whenever I need some Cygwin functionality on my Windows hosts, I always prefer pre-packaged solutions (
Mobaxterm for ssh client on Windows, CopSSH for SSHD, etc.). This time around I needed a free SSH server for Windows 2012R2 host without the limits imposed by recent CopSSH free version. I decided that I’ll try to use SSHD from cygwin.com directly, something that I tried to avoid in the last decade.
1) INSTALLATION
First you’ll need to download installer from
cygwin.com, save the file in some temporary directory. I downloaded 64-bit version because I’ll be installing 64-bit packages. More precisely, I selected the following packages and their dependencies: nano, zip, unzip, OpenSSH, openssl and rlwrap.
Run the installer and follow the wizard, here are screenshots from my host:
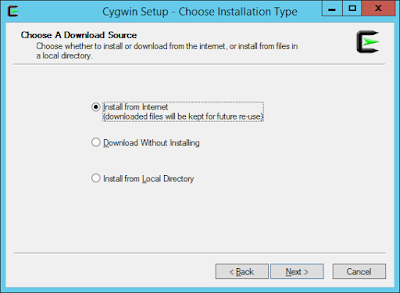
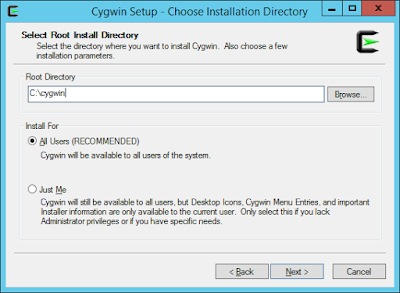
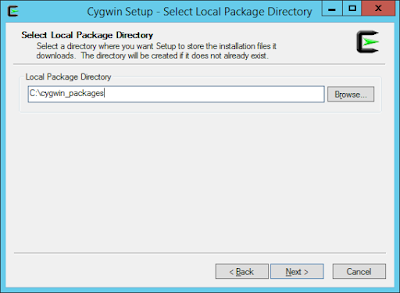
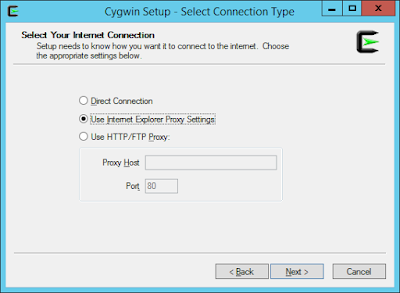
 2) CONFIGURATION
2.1) Should we edit cygwin.bat?
2) CONFIGURATION
2.1) Should we edit cygwin.bat?
You’ll probably find numerous recommendation on the net (and even in Oracle documentation — “Enterprise Manager Cloud Control Basic Installation Guide”) that first thing you should do is to open cygwin.bat and insert line set CYGWIN=binmode ntsec, so that bat would look like:
notepad c:\cygwin\cygwin.bat
|
@echo off
C:ssh
chdir C:\cygwin\bin
set CYGWIN=binmode ntsec << INSERTED LINE
bash --login -i
|
Open C:\cygwin\cygwin.bat and run:
And you should see help for cygwrunsrv, otherwise something went wrong and you’ll likely have to re-install.
2.3 Configure SSHD service by opening cygwin.bat with “Run as Administrator” privilege:
*** Info: Generating missing SSH host keys
ssh-keygen: generating new host keys: RSA1 RSA DSA ECDSA ED25519
*** Info: Creating default /etc/ssh_config file
*** Info: Creating default /etc/sshd_config file
*** Info: StrictModes is set to 'yes' by default.
*** Info: This is the recommended setting, but it requires that the POSIX
*** Info: permissions of the user's home directory, the user's .ssh
*** Info: directory, and the user's ssh key files are tight so that
*** Info: only the user has write permissions.
*** Info: On the other hand, StrictModes don't work well with default
*** Info: Windows permissions of a home directory mounted with the
*** Info: 'noacl' option, and they don't work at all if the home
*** Info: directory is on a FAT or FAT32 partition.
*** Query: Should StrictModes be used? (yes/no) yes
*** Info: Privilege separation is set to 'sandbox' by default since
*** Info: OpenSSH 6.1. This is unsupported by Cygwin and has to be set
*** Info: to 'yes' or 'no'.
*** Info: However, using privilege separation requires a non-privileged account
*** Info: called 'sshd'.
*** Info: For more info on privilege separation read /usr/share/doc/openssh/README.privsep.
*** Query: Should privilege separation be used? (yes/no) yes
*** Info: Note that creating a new user requires that the current account have
*** Info: Administrator privileges. Should this script attempt to create a
*** Query: new local account 'sshd'? (yes/no) yes
*** Info: Updating /etc/sshd_config file
*** Query: Do you want to install sshd as a service?
*** Query: (Say "no" if it is already installed as a service) (yes/no) yes
*** Query: Enter the value of CYGWIN for the daemon: [] binmode ntsec
*** Info: On Windows Server 2003, Windows Vista, and above, the
*** Info: SYSTEM account cannot setuid to other users -- a capability
*** Info: sshd requires. You need to have or to create a privileged
*** Info: account. This script will help you do so.
*** Info: It's not possible to use the LocalSystem account for services
*** Info: that can change the user id without an explicit password
*** Info: (such as passwordless logins [e.g. public key authentication]
*** Info: via sshd) when having to create the user token from scratch.
*** Info: For more information on this requirement, see
*** Info: https://cygwin.com/cygwin-ug-net/ntsec.html#ntsec-nopasswd1
*** Info: If you want to enable that functionality, it's required to create
*** Info: a new account with special privileges (unless such an account
*** Info: already exists). This account is then used to run these special
*** Info: servers.
*** Info: Note that creating a new user requires that the current account
*** Info: have Administrator privileges itself.
*** Info: No privileged account could be found.
*** Info: This script plans to use 'cyg_server'.
*** Info: 'cyg_server' will only be used by registered services.
*** Query: Do you want to use a different name? (yes/no) no
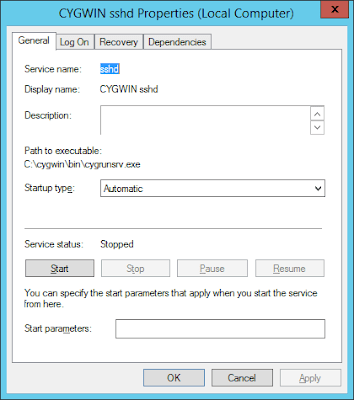
*** Query: Create new privileged user account 'ACMEHOST\cyg_server' (Cygwin name: 'cyg_server')? (yes/no) yes
*** Info: Please enter a password for new user cyg_server. Please be sure
*** Info: that this password matches the password rules given on your system.
*** Info: Entering no password will exit the configuration.
*** Query: Please enter the password: mysecret
*** Query: Reenter:
*** Info: User 'cyg_server' has been created with password 'mysecret'.
*** Info: If you change the password, please remember also to change the
*** Info: password for the installed services which use (or will soon use)
*** Info: the 'cyg_server' account.
*** Warning: Expected privileged user 'cyg_server' does not exist.
*** Warning: Defaulting to 'SYSTEM'
*** Info: The sshd service has been installed under the LocalSystem
*** Info: account (also known as SYSTEM). To start the service now, call
*** Info: `net start sshd' or `cygrunsrv -S sshd'. Otherwise, it
*** Info: will start automatically after the next reboot.
*** Info: Host configuration finished. Have fun!
|
Note the line 33:
*** Query: Enter the value of CYGWIN for the daemon: [] binmode ntsec
|
Here you should enter any env. variables for cygwin daemon if any. I did NOT set those two variables, they’re here only as a note point. According to cygwin documentation, both parameters are obsolete since Cygwin 1.7, I believe the only reason both parameter are still listed, even in Oracle current documentation, is that someone found some old “how-to” on the net (which was valid before 1.7 release) and took it as granted.
After configuration you should check services, you should see CYGWIN sshd….
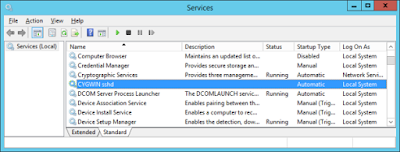
and two new local accounts, cyg_server and sshd…
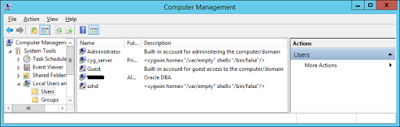 2.4) Enable existing local user account to connect to SSH daemon
2.4) Enable existing local user account to connect to SSH daemon
// take a backup if by any chance you already have a passwd file (not the case for fresh installation!)
copy C:\cygwin\etc\passwd C:\cygwin\etc\passwd.bak
|
Open cygwin.bat:
$ /bin/mkpasswd -l -u alesk >> /etc/passwd
|
The above command will write something like this in the passwd file:
ACMEHOST+alesk:*:197610:197121:U-ACMEHOST\alesk,S-1-5-21-1611771360-925472152-3555864332-1002:/home/alesk:/bin/bash |
It means that you can connect to ACMEHOST from some remote workstation with:
$ ssh ACMEHOST+alesk@ACMEHOST
|
Not cool. I prefer using, simple:
$ ssh alesk@acmehost
so, I changed the username in /etc/passwd to:
alesk:*:197610:197121:U-ACMEHOST\alesk,S-1-5-21-1611771360-925472152-3555864332-1002:/home/alesk:/bin/bash
|
And for a domain account you would execute:
$ /bin/mkpasswd -d -u alesk >> /etc/passwd
$ mkdir -p /home/alesk
$ chown alesk /home/alesk
|
2.5) Edit ssh config file
notepad C:\cygwin\etc\sshd_config
|
or within cygwin.bat:
At the end of file add:
KexAlgorithms diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1
|
I’m not sure what is the true reasoning for that, but probably for hardening the sshd security!?
2.6) Start SSH daemon
Cygwin.bat
or
or start Windows service
Open cmd.exe with “Run as admninistrator”:
|
cmd> net stop "CYGWIN sshd"
cmd> net start "CYGWIN sshd"
|
If service doesn’t start check the log at C:\cygwin\var\log\sshd.log.
If you need to add some package afterwards, simply re-run setup.exe installer and check additional packages that you want to install.