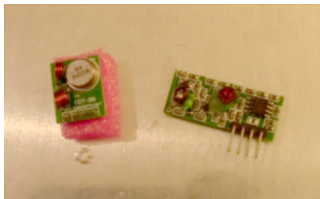
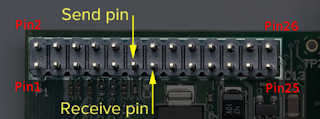
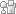WiringPi GPIO pins

Pin 2 - Vcc (5V)
Pin 6 - GND
Pin 11 - GPIO 17 - (WiringPi Pin 0): Linked to Emitter
Pin 13 - GPIO 27 - (WiringPi Pin 2): Linked to Receiver (RF433MHz – XY-MK-5V)

FROM: http://i-build-stuff.blogspot.com.es/2015/01/wireless-room-temperature-monitoring_27.html
With that simple setup on i can go ahead i can try and send data and see if it is being received.
Now on my computer i connect to my Raspberry Pi using ssh
Code 1 : ssh pi@yourlocalIPaddress
|
(once prompted, enter your password. Default is "raspberry")
Then I have to go to the specific folder where the 433Utils programs are stored in order to start them.
Code 2 : cd 433Utils/RPi_utils
|
This bring you to the correct folder where the sending program and the sniffing program are stored.
Now i open another Terminal window and login via ssh (code 1) and i go to the 433Utils folder (code 2)
In the first terminal window start the Sniffer program.
Code 3 : sudo ./RFSniffer
|
Now in the second terminal window send a code
Code 4 : sudo ./codesend 121234 (any random integer)
|
If everything works fine, you should see your integer going through the Sniffer result window just like in the below screenshot :
pi@raspberrypi ~/wiringPi $ gpio readall
|
(*) Raspberry Pi RF remote (433MHz)
FROM: http://npham.dk/?p=34
Creating RF transmitter / receiver
Source: http://shop.ninjablocks.com/blogs/how-to/7506204-adding-433-to-your-raspberry-pi
I bought my RF transmitter and receiver from
eBay a about 1$.
Connecting RF transmitter and receiver to the Raspberry Pi is pretty simple.
Both the reciver and transmitter has a VCC, GND and DATA pins.
And all you do is connect it to the Raspberry Pi GPIO pins.
 Install RPi_utils
Install RPi_utils
Source:
https://github.com/ninjablocks/433Utils/tree/master/RPi_utils
Start by installing RPI_utils
#Installs GIT
sudo apt-get install git
sudo apt-get install git-core
|
#Installs 433utils
git clone git://github.com/ninjablocks/433Utils.git
cd 433Utils/RPi_utils/
|
#Installs wiringPI
git clone git://git.drogon.net/wiringPi
cd wiringPi
git pull origin
./build
|
#Builds RPI_util
Testing and decoding RF signal
To capture and decode the RF signal from the remote, I ran the program RFSniffer.
When I push the A (on) button on the remote, I get the following code on the screen.
Received 5260625
Received 5260625
Received 5260625
Received 5260625
Received 5260625
|
To test if the transmitter works you can send the received value with this command.
If you convert 5260625 to binary, you get 10100000100010101010001.
And looking at the binary value of all the buttons, you start to see a pattern.
Button Decimal value Binary value
A (On) 5260625 10100000100010101010001
A (Off) 5260628 10100000100010101010100
B (On) 5263697 10100000101000101010001
B (Off) 5263700 10100000101000101010100
C (On) 5264465 10100000101010001010001
C (Off) 5264468 10100000101010001010100
D (On) 5264657 10100000101010100010001
D (Off) 5264660 10100000101010100010100
|
They all starts with 1010000010, and all the ON buttons ends with 0001 and all the OFF buttons ends with 0100.
The 1010000010 matches with the dip-switches; 10 = down and 01 = up.
The middle part, is a value that identifies A,B,C and D.
You can see the pattern here:
Dip switch Button Id On / Off
A = 10 10 00 00 10 + 00 10 10 10 1 + 0001 / 0100
B = 10 10 00 00 10 + 10 00 10 10 1 + 0001 / 0100
C = 10 10 00 00 10 + 10 10 00 10 1 + 0001 / 0100
D = 10 10 00 00 10 + 10 10 10 00 1 + 0001 / 0100
|
Script
I then created the following bash script.
#!/bin/bash
BTN=$1
STATUS=$2
BTN=$(echo $BTN | tr '[:lower:]' '[:upper:]')
STATUS=$(echo $STATUS | tr '[:lower:]' '[:upper:]')
DIP_SWITCH="DDUUD" #Change dip switches to match the remote
#hardcoded values
BTN_A="001010101"
BTN_B="100010101"
BTN_C="101000101"
BTN_D="101010001"
DIP_SWITCH=$(echo $DIP_SWITCH | sed 's/D/10/g' | sed 's/U/00/g')
case $BTN in
A )
BTN=$BTN_A ;;
B )
BTN=$BTN_B ;;
C )
BTN=$BTN_C ;;
D )
BTN=$BTN_D ;;
* )
echo "Please define the button [A-D]";exit;
esac
case $STATUS in
ON )
STATUS="0001" ;;
OFF )
STATUS="0100" ;;
* )
echo "Please define the button state [ON/OFF]";exit;
esac
BIN=$(echo $DIP_SWITCH$BTN$STATUS)
DEC=$((2#$BIN))
#echo $DEC
sudo /home/pi/codesend $DEC
|
And to emulate a click, I just call
Control via web
Because the codesend uses wiringpi, it is required to call with sudo.
But if you need to call it from a webserver, it creates some problem, because sudo requires a password.
So we need to edit visudo, so it doesn’t require a password.
(it may not be a secure thing to do, but in my case the webserver is not exposed to the internet, and is only for “at home” use)
Add the following line to the file.
#NOTE: use TAB and not space, except for the last one – after NOPASSWD:
www-data ALL=(root) NOPASSWD: /home/pi/433Utils/RPi_utils/codesend
|
Save the file and reboot the Raspberry Pi, and you’re good to go.
Now the local PHP webserver can call the script with:
< ? php
shell_exec("/home/pi/433Utils/RPi_utils/RFISend.sh A ON");
? >
|
http://rsppi.blogspot.com.es/2013/08/comunicacion-por-rf-433mhz-desde.html
Home Control Dashboard
https://dendriticspine.github.io/projects/2014/10/10/homedashboard
REFERENCE:
http://www.touteladomotique.com/forum/viewtopic.php?f=118&t=15760
http://wiringpi.com/wp-content/uploads/2013/03/pins.pdf
WiringPi GPIO pins
http://www.14core.com/configure-clibrary-wiringpi/
http://blogwifi.fr/raspberry-pi-b-telecommande-433-mhz-universelle/
http://domotique-home.fr/domotique-diy-partie-2-protocole-433-mhz/
http://npham.dk/?p=34
http://www.princetronics.com/how-to-read-433-mhz-codes-w-raspberry-pi-433-mhz-receiver/