Setup OpenSSH (Cygwin) for public key authentication
From: dbaportal.eu
(Thanks to alesk for his great job)
It took me awhile to realize that my SSHD installation on my Windows 2012R2 was not ready yet to accept public key authentication, which is a key feature.
If we want to automate some tasks we need passwordless authentication to our Windows 2012 R2 server.
By default sshd is running under Local System account and this is in conflict with implementation of public key authentication of OpenSSH in Cygwin. If you recollect from my last post, special account was created, called cyg_server:
(Thanks to alesk for his great job)
It took me awhile to realize that my SSHD installation on my Windows 2012R2 was not ready yet to accept public key authentication, which is a key feature.
If we want to automate some tasks we need passwordless authentication to our Windows 2012 R2 server.
By default sshd is running under Local System account and this is in conflict with implementation of public key authentication of OpenSSH in Cygwin. If you recollect from my last post, special account was created, called cyg_server:
*** Info: On Windows Server 2003, Windows Vista, and above, the
|
The important info is this:
*** Info: It’s not possible to use the LocalSystem account for services
|
So, the first thing that we need to do is to stop “CYGWIN sshd” service and change logon account for the sshd service as shown on the following screenshots:
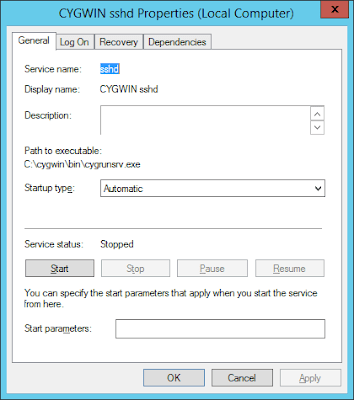
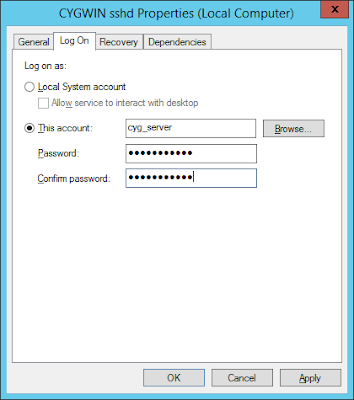
At this point you can not start the service yet, if you try you’ll find in /var/log/sshd.log the following error:
/var/empty must be owned by root and not group or world-writable.
|
What we need to do is to change owner of the directory /var/empty from SYSTEM to cyg_server. Open cygwin.bat and run:
// check current permissions
|
At this point you should be able to start “CYGWIN sshd” service under local cyg_server account. The last thing you need to do is to test the connection with public key authentication. I used Mobaxterm for that on my workstation ACMEWKS, but you could as easily use Cygwin SSH on your workstation:
In MobaXterm window:
We need to generate some public-private keys. Note that in our case we need PK keys for passwordless authentication, so we didn't password protect rsa private key in the example that follows.
[alesk.ACMEWKS] ? ssh-keygen -t rsa
|
Remember, that /home/mobxterm/.ssh is volatile, after you close the MobaXterm this directory is gone, so you should copy public/private keys to some local, permanent directory....
[alesk.ACMEWKS] ? ls -al /home/mobaxterm/.ssh
|
Now, we can try to connect from ACKMEWKS to ACMEHOST with PK authentication:
[alesk.ACMEWKS] ssh -i /cygdrive/g/ssh/id_rsa alesk@ACMEHOST
|
You should be logged on ACMEHOST without prompt for a password. Properly protect private key. Better yet, you should limit what someone can execute execute via passwordless ssh connection with the help of prefix in authorized_keys file for each public key (see this for an example).
And finally, you can troubleshoot ssh connection by turning on verbose mode (-v, -vvv), for example:
[alesk.ACMEWKS] ssh -vvv -i /cygdrive/g/ssh/id_rsa alesk@ACMEHOST
|








0 comentarios:
Post a Comment